Check Point researchers have discovered multiple security vulnerabilities in Fortnite, a massively popular online battle game, one of which could have allowed remote attackers to completely takeover player accounts just by tricking users into clicking an unsuspectable link.
The reported Fortnite flaws include a SQL injection, cross-site scripting (XSS) bug, a web application firewall bypass issue, and most importantly an OAuth account takeover vulnerability.
Full account takeover could be a nightmare, especially for players of such a hugely popular online game that has been played by 80 million users worldwide, and when a good Fortnite account has been sold on eBay for over $50,000.
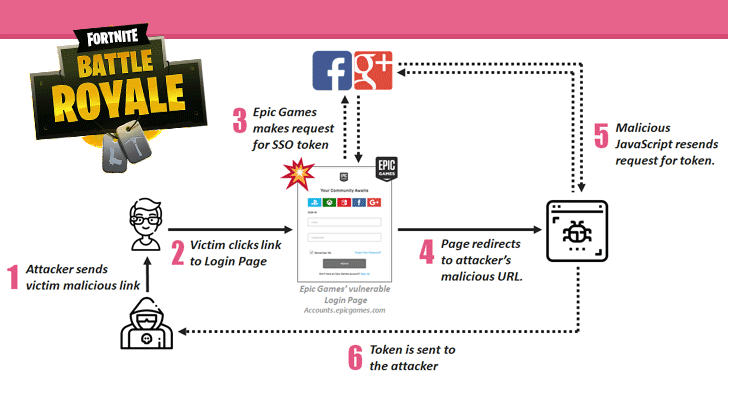
The Fortnite game lets its players log in to their accounts using third-party Single Sign-On (SSO) providers, such as Facebook, Google, Xbox, and PlayStation accounts.
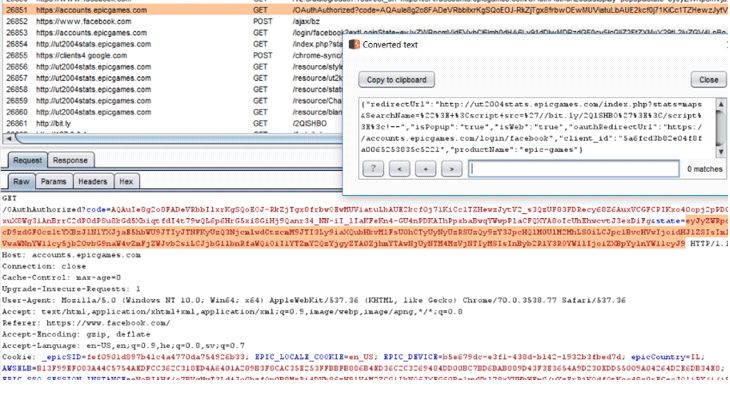
According to the researchers, the combination of cross-site scripting (XSS) flaw and a malicious redirect issue on the Epic Games’ subdomains allowed attackers to steal users’ authentication token just by tricking them into clicking a specially crafted web link.
Once compromised, an attacker can then access players’ personal information, buy in-game virtual currencies, and purchase game equipment that would then be transferred to a separate account controlled by the attacker and resold.
“Users could well see huge purchases of in-game currency made on their credit cards with the attacker funneling that virtual currency to be sold for cash in the real world,” Check Point researchers explain in their blog post published today.
“After all, as mentioned above we have already seen similar scams operating on the back of Fortnite popularity.”
The attacker even could have access to all the victim’s in-game contacts and conversations held by the player and his friends during the game, which can then be abused to exploit the account owner’s privacy.
One of the Epic Games’ contained a SQL injection vulnerability, which if exploited, could have allowed attackers to identify which version of MySQL database was being used.
Besides this, the researchers were also able to bypass the BIG-IP Application Security Manager (ASM) web application firewall system used by the Fortnite infrastructure to successfully execute the cross-site scripting attack against the user login process.
Check Point researchers notified Epic Games’ developer of the Fortnite vulnerabilities which the company fixed in mid-December.
Both Check Point and Epic Games recommend all Fortnite users to remain vigilant while exchanging any information digitally and to question the legitimacy of links to information available on the User Forum and other Fortnite websites.
To protect their accounts from being hijacked, players are also advised to enable two-factor authentication (2FA) which prompts users to enter a security code sent to their email upon logging into the Fortnite game.