Tag: HACKING
Install Kali Linux 2020.4 – Step by Step with Screenshots
Kali Linux 2020.4 release is now available for immediate download. Kali Linux is an Advanced Penetration Testing Linux distribution suited for Ethical hacking, Penetration Testing, and network security assessments...
Microsoft: Hackers have accessed source code for Azure and Exchange
In connection with the extensive SolarWinds Attack at the turn of the year, hackers managed to access Microsoft's internal network and downloaded certain files.
Microsoft's security department has released a...
Hackers tried to poison the water for 15,000 people
First, the hackers attacked the software that controls the water supply in a city in Florida. Then they tried to increase the amount of sodium hydroxide, lye, in the...
Hackers pulled in close to 400 million in bug hunting in 2019
Swedish hackers collected approximately 8.5 million in rewards for detected security deficiencies during the past year.
2019 was a good year financially for ethical hackers, sometimes also called white hats....
Canon DSLR Cameras Can Be Hacked With Ransomware Remotely
The threat of ransomware is becoming more prevalent and severe as attackers' focus has now moved beyond computers to smartphones and other Internet-connected smart devices.
In its latest research, security...
This Flaw Could Have Allowed Hackers to Hack Any Instagram Account Within 10 Minutes
Watch out! Facebook-owned photo-sharing service has recently patched a critical vulnerability that could have allowed hackers to compromise any Instagram account without requiring any interaction from the targeted users.
Instagram...
Chinese Hacker Publishes PoC for Remote iOS 12 Jailbreak On iPhone X
Here we have great news for all iPhone Jailbreak lovers and concerning one for the rest of iPhone users.A Chinese cybersecurity researcher has today revealed technical details of critical...
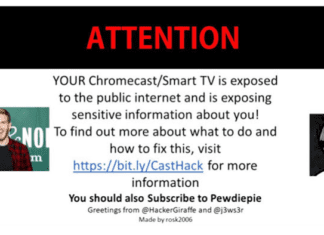
Thousands of Google Chromecast Devices Hijacked to Promote PewDiePie
A group of hackers has hijacked tens of thousands of Google's Chromecast streaming dongles, Google Home smart speakers and smart TVs with built-in Chromecast technology in recent weeks by...
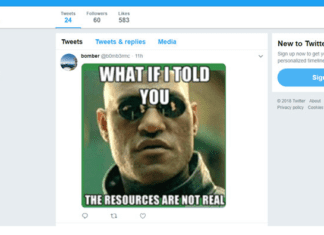
New Malware Takes Commands From Memes Posted On Twitter
Security researchers have discovered yet another example of how cybercriminals disguise their malware activities as regular traffic by using legitimate cloud-based services.Trend Micro researchers have uncovered a new piece...
Mayday! NASA Warns Employees of Personal Information Breach
Another day, another data breach. This time it's the United States National Aeronautics and Space Administration (NASA)
NASA today confirmed a data breach that may have compromised personal information of...