Tag: SECURITY
Ghost-telefonen som Blev Hackad – När Säkerhetens Gränser Testades
Hyra-ett-spöke
Ghost-telefoner såldes för cirka 25 000 kronor, vilket inkluderade ett sex månaders abonnemang på ett krypterat nätverk och teknisk support via ett återförsäljarnätverk.
Ghosts mobiltelefon- och datorapplikation påstås erbjuda användarna...
Install Kali Linux 2020.4 – Step by Step with Screenshots
Kali Linux 2020.4 release is now available for immediate download. Kali Linux is an Advanced Penetration Testing Linux distribution suited for Ethical hacking, Penetration Testing, and network security assessments...
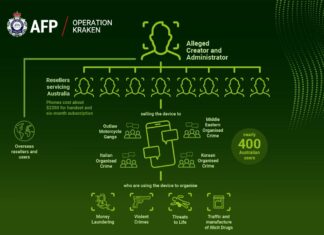
Hackers selling intrusion a growing threat
A group of cyber-criminals who have received a real boost under the corona are those called access brokers - they hack into systems and then sell the access on...
Microsoft: Hackers have accessed source code for Azure and Exchange
In connection with the extensive SolarWinds Attack at the turn of the year, hackers managed to access Microsoft's internal network and downloaded certain files.
Microsoft's security department has released a...
Security flaw in Android app downloaded a billion times
The shortcomings are due to the app lacking proper restrictions on who can access its code.
Security researchers at Trend Micro have discovered that the file sharing app Shareit for...
Hackers tried to poison the water for 15,000 people
First, the hackers attacked the software that controls the water supply in a city in Florida. Then they tried to increase the amount of sodium hydroxide, lye, in the...
The Cyberpunk 2077 developer’s hacked data have been resold
It is unclear who the buyer is and what they intend to do with the data.
Earlier this week The Witcher developer CD Projekt Red had been hacked and that...
Hackers can use ordinary light bulbs to spy
Can use a standard incandescent light to intercept calls at a distance of 25 meters.
As if it wasn't bad enough that the email, computer and mobile are vulnerable to...
German hacker created gigantic botnet to download anime
By exploiting a vulnerability in D-Link's firmware, a man named Stefan was able to access tens of thousands of network devices over eight years.
According to a new report from...
The new Trojan Eventbot spies on your banking apps
In the long term, the new tax program could become one of the biggest threats to our mobile phones.
Researchers at security company Cybereason are warning of Eventbot, a new...